Threat Modeling with ChatGPT
How AI can help us understand the threats we care about, with a step-by-step example for Azure and sample prompts to get started
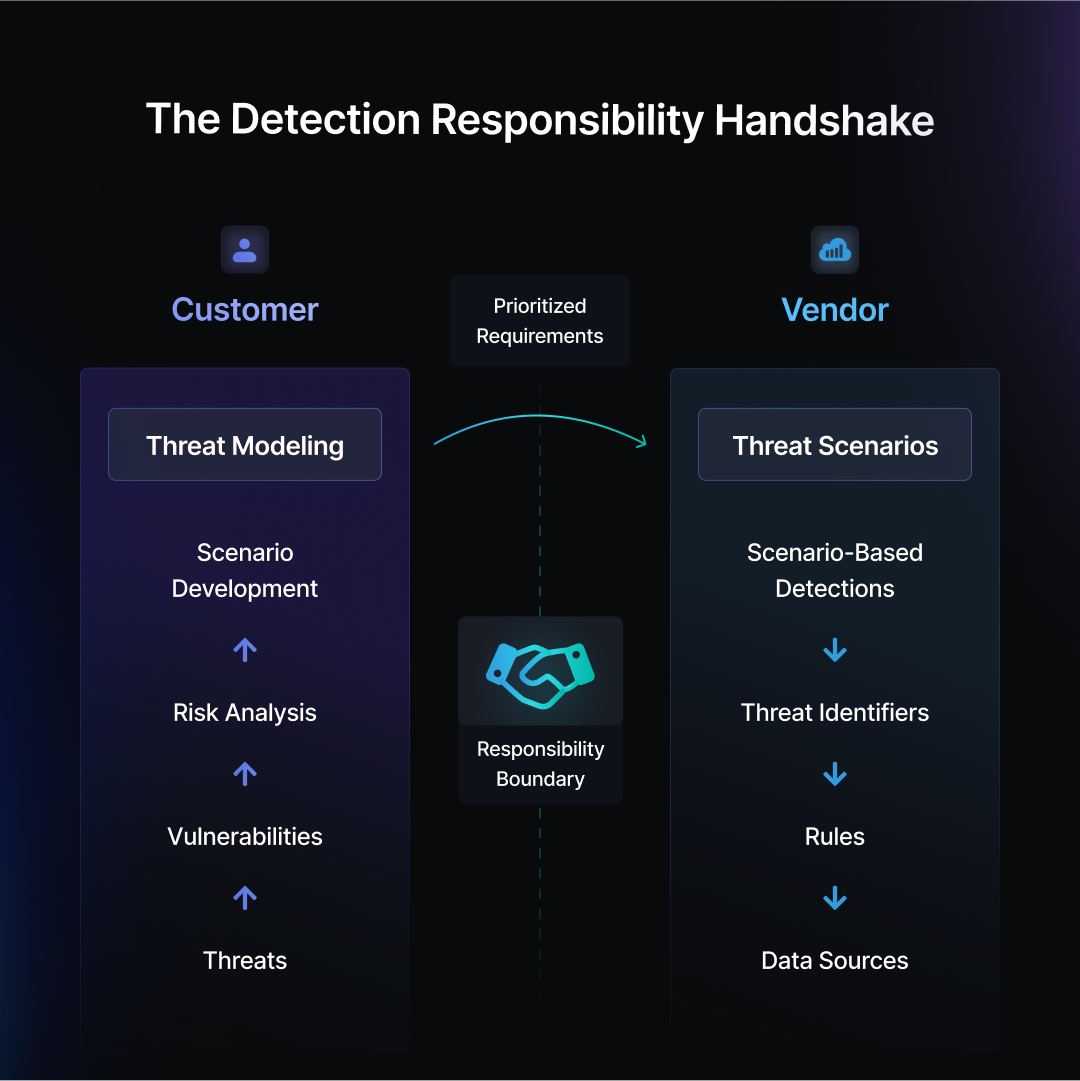
SOC leaders need threat models like architects need blueprints. However, some feedback to my post on The Detection Responsibility Handshake was that security operations are short on threat models. Many lack the experience or time to begin threat modeling. Let's explore how AI can help.
A New Application for LLMs
ChatGPT, with its latest release, emerges as a powerful assistant for threat modeling. This tool is not just a repository of information; it's a dynamic resource adept at understanding and applying cybersecurity best practices. With a deep background in cloud architecture details, modern attacker techniques, and reasoning capabilities around probability and impact, ChatGPT can be a great resource for cybersecurity planning initiatives.
Threat modeling is a strategic process that involves identifying, assessing, and addressing potential threats in a proactive manner to combat cyber risks. This approach shifts the paradigm from a reactive to a proactive defense, making it easier for organizations to anticipate and mitigate threats before they can cause any damage. Given that it is not feasible to address every possible threat, the goal is to prepare for those threats that are most likely to occur and have a significant negative impact.
Many organizations, while recognizing the importance of threat modeling, often find themselves constrained by resources and time. This is where ChatGPT can play a transformative role. By leveraging AI, organizations can streamline their threat modeling processes, making them more efficient and effective. This blog will delve into how ChatGPT can be applied in the context of securing modern cloud-centric environments. We’ll use Azure as an example, but this article's approach can be applied to any environment where you are responsible for detecting and responding to threats.
With the help of tools like ChatGPT, threat modeling need not be a daunting task. Instead, it can be an integrated, manageable, and even streamlined part of your security operations, informing your detection engineering strategy and overall cybersecurity posture.
Integrating ChatGPT in Threat Modeling
Large language models (LLMs) are good at going from a small prompt to a broad response that covers an entire topic. ChatGPT is a pro at synthesizing large amounts of information based on what it knows about cybersecurity and modern information systems. This is a crucial ability in threat modeling, where understanding the landscape is half the battle.
However, it's important to remember that ChatGPT is an AI tool, not a silver bullet. It can't replace human judgment, intuition, and experience. While it can suggest possible risks to consider, the final assessment and decision-making rest with us cybersecurity professionals.
As we’ll see in the following threat modeling exercise, the security engineer provides the context, sets the boundaries for the exercise, and interprets ChatGPT’s output through the lens of their organization’s specific needs and challenges. This requires organizational knowledge and strategic decision-making that the robots are not going to do for us. The goal of integrating ChatGPT in threat modeling is to form a symbiotic relationship where AI capabilities complement the expertise and contextual understanding of the security team.
In the next section, we'll work through a step-by-step example of harnessing ChatGPT for threat modeling for an Azure environment. This guide will help you navigate the process, from setting up ChatGPT to using its outputs for effective threat modeling and risk prioritization. The results can guide your detection engineering, the solutions you onboard, and how you use them.
Step-by-Step Example: Threat Modeling Azure Cloud
Step 1: Set the environment
To effectively utilize ChatGPT as an assistant for threat modeling, start by clearly defining the scope of the exercise. Here we are threat modeling your hypothetical Azure environment. This involves identifying the services you use, the nature of your deployments, and any specific configurations unique to your organization. This information is provided via a prompt. The goal is to give ChatGPT a comprehensive view of your Azure landscape. This baseline understanding is crucial for ChatGPT to generate relevant and contextual threat models.
Prompt: "ChatGPT, I need to conduct threat modeling for a hypothetical Azure cloud environment that uses Azure Active Directory, Azure Storage, and Azure Virtual Machines with a mix of IaaS and PaaS and custom security configurations. Can you provide an overview of potential threat areas?"
ChatGPT Response: "In your Azure environment, potential threat areas include:
Misconfigurations in Azure Storage leading to unauthorized data access.
Insecure management of credentials in Azure Active Directory.
Vulnerabilities in custom configurations that may lead to exploitation.
Risks associated with the integration of IaaS and PaaS, such as insufficient isolation.
Security gaps in Virtual Machines, including unpatched OS or applications."
Step 2: Define the threats
Once ChatGPT is configured with your Azure environment details, the next step is to ask it to identify potential threats. ChatGPT, drawing from its vast knowledge base, can enumerate a list of common and emerging threats specific to Azure. These can range from misconfigured storage accounts to potential security loopholes in Azure Active Directory. This list serves as a starting point for deeper analysis.
Your organization's past experiences and existing threat intelligence are invaluable. Share this information with ChatGPT to refine the threat list further. This step ensures that the model considers theoretical threats and those you have previously encountered or are more likely based on your industry and history.
Prompt: "ChatGPT, could you identify potential threats for our Azure environment that include remote file inclusion attacks on virtual machines and unauthorized access to cloud service accounts due to exposure of access keys in a code repository?"
ChatGPT Response: "Potential threats for your Azure environment:
Remote File Inclusion (RFI) attacks targeting virtual machines, allowing attackers to execute malicious scripts or drop malware.
Threats from exposed cloud service account access keys, possibly due to accidental code repository exposure, leading to unauthorized access and control over Azure services.
Risks of data breaches or service disruption stemming from these vulnerabilities."
Step 3: Consider known vulnerabilities
No production environment is 100% locked down. Review vulnerability scans, CSPM findings, and audit reports for known vulnerabilities or areas of concern within your Azure environment. This list could also include details about past incidents, areas where compliance is tricky, or parts of your infrastructure that have often been challenging to secure. ChatGPT can use this information to prioritize threats and tailor the threat model to your unique vulnerabilities.
Also provide ChatGPT with details about the key assets in your Azure environment – which might include databases, virtual machines, or application services – and their critical functionalities. Any system has inherent vulnerabilities and ways in which it can be abused by attackers and malicious insiders. This step helps ChatGPT understand which assets are most crucial and should be prioritized in the threat modeling process, as well as known issues that attackers could use to target these assets.
Remember to stay within your company’s security policies whenever handling sensitive information about security posture and vulnerabilities.
Prompt: "ChatGPT, given the threats, assets, and vulnerabilities we've discussed in our Azure environment, can you analyze and prioritize the top risks to our organization?"
ChatGPT Response: "Based on the discussion about your Azure environment's threats, assets, and vulnerabilities, here's an analysis and prioritization of the top risks:
Risk to Outdated Operating Systems in Virtual Machines:
Priority: High
Rationale: The presence of known vulnerabilities in outdated OS makes these systems highly susceptible to attacks. The potential for unauthorized access and subsequent network compromise poses a significant risk to the organization.
Risk to Customer Database:
Priority: Very High
Rationale: The database contains sensitive customer information. Vulnerabilities here pose a grave risk due to the potential for substantial data breaches, leading to severe privacy and legal implications.
Risk to Payment Processing Service:
Priority: High
Rationale: Given its critical role in operations, any compromise in this service could lead to operational disruptions and loss of customer trust. While it might be better protected than other assets, the impact of a breach here would be considerable.
Each of these risks requires immediate attention, with prioritized efforts towards securing the customer database due to its potential for the most direct and severe impact on the organization."
Step 4: Analyze the risks
With a comprehensive list of threats and vulnerabilities, use ChatGPT to analyze and rank these risks based on their likelihood and potential impact. This analysis will help you focus on the most significant threats, ensuring that your detection engineering resources are allocated efficiently.
Prompt: "ChatGPT, analyze and prioritize the top risks for our organization based on the discussed threats, assets, and vulnerabilities in our Azure environment."
ChatGPT Response: "Considering the various factors in your Azure environment, here's an analysis and prioritization of the top risks:
Risk Associated with Outdated Operating Systems in Virtual Machines:
Priority: High
Rationale: The risk is significant due to the ease of exploiting known vulnerabilities in outdated systems. The impact includes potential unauthorized access, data breaches, and further network compromise.
Risk to the Customer Database:
Priority: Very High
Rationale: This risk stands out due to the sensitivity of the data involved. A breach here could lead to severe privacy violations, legal implications, and reputational damage. It's imperative to secure this asset due to the direct and severe impact on the organization.
Risk to Payment Processing Service:
Priority: High
Rationale: While potentially well-secured, the critical nature of this service means any compromise could disrupt operations and damage customer trust. The impact of a breach here, though potentially less direct than the customer database, is still considerable due to operational and financial implications.
The prioritization highlights the urgent need to address vulnerabilities in the customer database and outdated operating systems, followed by reinforcing the security of the payment processing service. Each risk presents unique challenges and should be managed with specific, tailored security measures."
Step 5: Create threat scenarios
Finally, leverage ChatGPT to develop detailed threat scenarios for the highest-ranked risks. These scenarios should include the potential attack vectors, the likely course of an attack, and the possible impact on your Azure environment. These scenarios will be instrumental in planning your defense strategies and ensuring that your security measures are as relevant and effective as possible.
Prompt: "Considering our risk analysis, could you develop detailed threat scenarios for our Azure environment that focus on the risks associated with outdated operating systems in virtual machines, vulnerabilities in the customer database, and the payment processing service?"
ChatGPT Response: "Certainly. Based on the prioritized risks, here are the detailed threat scenarios for your Azure environment:
Outdated Operating Systems in Virtual Machines:
Scenario: An attacker exploits a vulnerability in the outdated OS of a virtual machine. This breach allows the attacker to gain unauthorized access, potentially installing malware or using the VM as a pivot point for lateral movement within the network.
Detection Focus: Monitor for signs of unusual activity, such as unexpected system access, changes in file integrity, or unusual network traffic patterns originating from these VMs.
Customer Database Vulnerabilities:
Scenario: A cybercriminal discovers and exploits a security flaw in the database, gaining unauthorized read and write access. The attacker could then exfiltrate sensitive customer data or manipulate database entries, leading to data integrity issues.
Detection Focus: Implement stringent monitoring of database access logs, look for anomalous query patterns, and set up alerts for data extraction activities that deviate from the norm.
Payment Processing Service Vulnerabilities:
Scenario: An intruder targets the payment processing service, aiming to intercept or alter transaction data. This could involve injecting malicious code or initiating unauthorized transactions.
Detection Focus: Keep a close watch on transaction logs, monitor for unexpected changes in transaction data or patterns, and track any unauthorized modifications to the service’s operational code.
Each scenario underscores the need for specific detection strategies, focusing on the most likely methods of exploitation and the potential impact of a breach. Implementing these targeted detection strategies will enhance your ability to identify and respond to incidents promptly, mitigating the risks to your Azure environment."
Next Steps and Limitations
With detailed threat scenarios in hand, the security operations team is in a position to work on what matters most. These scenarios can represent the requirements for monitoring the environment, driving the detection engineering backlog, tool selection, and which data sources should be collected.
It’s worth noting that this approach is the opposite of the “hoarding mentality” that often comes with new SOC initiatives such as starting a security data lake. In the example above, it’s clear that endpoint activity logs are less of a priority than network flow logs from the cloud environment, database monitoring records, or code change history. Those sources are urgent to collect because they support the detections that cover the threat scenarios we care about most.
While AI tools can provide valuable assistance with threat modeling, it's important to recognize their limitations. ChatGPT operates based on the data it has been trained on, and thus, it may not always be up-to-date with the latest threats or specific nuances of your unique environment. It should be viewed as a tool to augment, not replace, the expertise of cybersecurity professionals. Use ChatGPT to gather insights and generate ideas, but always couple these with human judgment and contextual understanding. Be mindful that AI-assisted threat modeling is part of a larger, comprehensive approach that includes human expertise, contextual analysis, and ongoing attention to developments in the threat landscape.
The significance of AI in cybersecurity, including ChatGPT, is expected to increase in the future. As the cybersecurity field matures, there will be a shift towards outcome-driven planning, where AI tools can help identify risks, model threats, predict incidents, and flag gaps. The integration of AI in cybersecurity operations will provide more dynamic, real-time decision-making capabilities, and better access to data, delivering value for the SOC. This, in turn, will drive initiatives to provide AI models with more access to information about the environment. To support this approach, SOCs will need a scalable and analytics-oriented architecture which can be achieved through the adoption of security data lakes. Therefore, security data lake adoption will play a key role in the shift toward AI-driven cybersecurity strategies.